The threat of phishing attacks continues to evolve and become increasingly sophisticated. One such emerging threat is the Tycoon 2FA Phishing Kit, which poses a significant challenge by bypassing multi-factor authentication (MFA) protections. Users of Microsoft 365 and Google Workspace are particularly vulnerable.
This blog aims to shed light on the Tycoon 2FA Phishing Kit, its potential consequences, and the underlying weaknesses in MFA systems that make them vulnerable to this type of attack. Additionally, we will explore the efforts made by the Sekoia Threat Detection and Research Team to mitigate this threat and provide best practices for strengthening defenses against Tycoon 2FA and similar phishing attacks.
Table of Contents
Understanding the Tycoon 2FA Phishing Kit
Phishing attacks have become increasingly sophisticated over the years, and hackers are constantly finding new ways to bypass security measures. One such method is through the use of 2FA phishing kits, which are specifically designed to overcome the additional security layer provided by two-factor authentication.
These kits work by mimicking legitimate login pages and prompting users to enter their credentials, along with the one-time passcodes generated by their authenticator apps or sent via SMS. This allows hackers to gain access to users’ accounts and bypass the additional security provided by 2FA.
In October 2023, Sekoia analysts discovered a new and widespread Adversary-in-The-Middle (AiTM) phishing kit called Tycoon 2FA. This Phishing-as-a-Service (PhaaS) platform has been actively used by multiple threat actors since at least August 2023 to conduct effective phishing attacks.
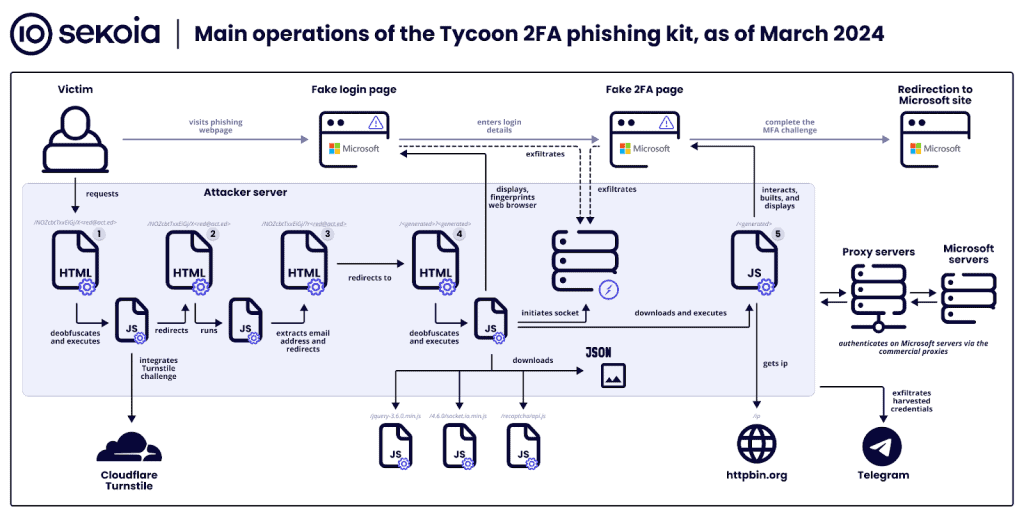
Tycoon 2FA has been identified as one of the most prevalent AiTM kits, with over 1,100 associated domains being uncovered between late October 2023 and late February 2024. This highlights the significant threat that this phishing kit poses to individuals and organizations.
In October 2023, there was an increase in phishing attacks using QR codes. This means that hackers were leveraging QR codes to direct users to malicious websites that mimic legitimate login pages. This shows the adaptability of hackers and their ability to constantly evolve their tactics.
Sekoia’s analysis of Tycoon 2FA and other AiTM phishing kits revealed several commonalities among these malicious pages. These similarities can help security professionals and organizations in identifying and defending against these types of attacks. These include:
- Deobfuscated scripts
- The use of CloudFlare Turnstile for protection
- Specific CSS resources.
It is important for cybersecurity professionals to stay updated on the latest phishing threats and cybersecurity measures. Understanding how these phishing kits work and the techniques used by hackers can help in implementing effective security measures and protecting sensitive information.
Further research on WebSockets, Microsoft pages, C2 servers, and other related topics can provide additional insights into the workings of these phishing kits and help in developing robust security strategies.
Overall, the discovery of the Tycoon 2FA phishing kit highlights the ongoing threat posed by phishing attacks and the need for individuals and organizations to remain vigilant and proactive in their cybersecurity efforts.
The Menace of MFA Bypass
The emergence of the “Tycoon 2FA” phishing-as-a-service (PhaaS) platform has posed a significant threat to the security of Microsoft 365 and Gmail email accounts. Threat actors have widely adopted this adversary-in-the-middle (AiTM) phishing kit to launch campaigns that can bypass multifactor authentication (MFA) protections. The Tycoon 2FA platform has been active since at least August 2022 and has recently been updated to enhance its obfuscation and anti-detection capabilities.
The primary goal of Tycoon 2FA is to harvest Microsoft 365 session cookies, allowing threat actors to bypass the MFA process during subsequent authentication. This means that even if users have enabled MFA for their accounts, the phishing campaign can still gain unauthorized access.
Between October 2023 and late February, the Tycoon 2FA platform has amassed over 1,100 domain names, indicating its widespread distribution and impact. This highlights the urgency for organizations using Microsoft 365 and Gmail to be vigilant and take additional measures to protect against this type of phishing attack.
To mitigate the risk of falling victim to Tycoon 2FA phishing campaigns, it is crucial for individuals to remain cautious and skeptical of any suspicious emails or requests for personal information, especially when it involves accessing sensitive accounts. Implementing additional security measures, such as using strong passwords, enabling two-factor authentication, and regularly undergoing security awareness training, can also help mitigate the risk.
Furthermore, organizations should consider implementing security products that can detect and block phishing attempts, as well as regularly update their security protocols to stay ahead of evolving threats. By staying informed and proactive in their approach to cybersecurity, individuals and organizations can better protect themselves against the menace of MFA bypass phishing campaigns facilitated by the Tycoon 2FA platform.
AiTM Phishing Kits and MFA Weakness
The W3LL phishing kit has emerged as a significant facilitator of global business email compromise (BEC) campaigns, with its primary targets being the manufacturing, information, and finance and insurance sectors. Operating through the underground marketplace known as the W3LL Store, this sophisticated phishing suite leverages various custom tools to bypass Multi-Factor Authentication (MFA) and infiltrate corporate Microsoft 365 accounts worldwide.
In a comprehensive threat report titled “W3LL Done Hidden Phishing Ecosystem Driving BEC Attacks,” cybersecurity firm Group-IB sheds light on the operations of a previously underexplored threat actor known as W3LL. The report provides valuable insights into the workings of the W3LL phishing kit, focusing on its tools and the underground marketplace where it thrives.
The W3LL phishing kit stands out due to its ability to bypass MFA, a security measure designed to add an extra layer of protection to user accounts. By exploiting weaknesses in MFA protocols, the kit enables cybercriminals to gain unauthorized access to corporate Microsoft 365 accounts, putting sensitive data at risk. This alarming capability has made the W3LL phishing kit a preferred choice for threat actors looking to carry out BEC campaigns.
The report highlights the sophistication of the phishing ecosystem created by the W3LL kit. It reveals the presence of custom tools such as Tycoon 2FA, Sekoia Threat Detection and Research team, and AiTM phishing kits, which allow attackers to mimic legitimate Microsoft pages and bypass security measures undetected. Additionally, the kit leverages C2 servers and WebSockets to maintain control over compromised accounts, making it difficult for security products to detect and mitigate the threat.
Ready-to-use templates provided by the W3LL phishing kit further streamline the phishing process, allowing even less technically skilled threat actors to launch successful campaigns. These templates mimic popular email services like Gmail, increasing the chances of recipients falling for the scam.
The W3LL phishing kit’s success can be attributed, in part, to weak security practices within targeted organizations. Despite the increasing adoption of MFA, many organizations fail to implement it properly, leaving their accounts vulnerable to attacks. This underscores the importance of robust security measures and regular employee training to mitigate the risks associated with phishing campaigns.
As the threat landscape continues to evolve, it is crucial for cybersecurity professionals, IT managers, and general tech enthusiasts to stay informed about the latest phishing threats. The insights provided by Group-IB’s report offer valuable knowledge that can help organizations better defend against BEC attacks facilitated by the W3LL phishing kit. By understanding the sophistication of these phishing operations and the weaknesses they exploit, proactive measures can be taken to enhance security and protect sensitive data.
Best Practices Against Tycoon 2FA Phishing
Tycoon 2FA is not a one of a kind PhaaS threat. Another threat that has recently come to light is a massive credential phishing attack campaign targeting top-level executives in over 100 organizations worldwide. This campaign leverages a phishing-as-a-service kit called EvilProxy, which was first exposed by cybersecurity company Resecurity in September 2022.
EvilProxy is a powerful tool that allows cybercriminals to run phishing attacks with reverse proxy capabilities, enabling them to steal credentials and bypass two-factor authentication (2FA) through adversary-in-the-middle techniques. With EvilProxy, any cybercriminal can easily acquire the kit and start using it through a simple interface that allows the creation of customizable phishing campaigns.
Organizations must understand the capabilities of EvilProxy and take necessary steps to strengthen their defenses against this type of phishing attack.
Best practices to protect your business from the threat of Tycoon 2FA and similar phishing attacks
1. Educate Employees: It is essential to educate employees about the risks of phishing scams and how to spot them. Regular training sessions and awareness programs can help employees recognize suspicious emails, websites, and requests for sensitive information.
2. Implement Multi-Factor Authentication: Enable and enforce the use of multi-factor authentication across all accounts and systems. This adds an extra layer of security and makes it more difficult for attackers to gain unauthorized access, even if they manage to steal credentials.
3. Regular Security Updates: Keep all software, applications, and operating systems up to date with the latest security patches. Cybercriminals often exploit vulnerabilities in outdated software, so regular updates are crucial to prevent potential breaches.
4. Use Security Products: Invest in robust security products, such as anti-phishing solutions and advanced threat detection systems. These tools can help detect and block phishing attempts, protecting your organization from potential data breaches.
5. Monitor and Analyze Network Traffic: Regularly monitor and analyze network traffic to identify any suspicious activities or anomalies. Implementing network traffic analysis tools can help detect and mitigate phishing attacks in real-time.
6. Report Suspicious Emails and Websites: Encourage employees to report any suspicious emails or websites to the IT department or the organization’s designated cybersecurity team. Prompt reporting can help prevent further spread of phishing attacks and enable faster response and mitigation.
7. Conduct Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify any weaknesses or gaps in your organization’s security infrastructure. Addressing these vulnerabilities proactively can help minimize the risk of falling victim to a phishing attack.
It is important to remember that cybersecurity is an ongoing effort, and staying updated with the latest threats and implementing robust security measures is crucial. Cybersecurity companies and researchers play a significant role in identifying and exposing new threats like EvilProxy, helping organizations stay one step ahead of cybercriminals.
Falling victim to a Tycoon 2FA phishing attack can have severe consequences for businesses and individuals, including financial losses, reputational damage, and potential data breaches. By following these best practices and staying vigilant, organizations can significantly reduce the risk of falling victim to phishing attacks and protect their valuable data and assets.
To Wrap Things Up
The rising threat of the Tycoon 2FA Phishing Kit highlights the constant need for vigilance and innovation in the field of cybersecurity. As attackers continue to find new ways to bypass multi-factor authentication protections, it is crucial for organizations and individuals to stay informed and implement best practices to strengthen their defenses. The insights provided by the Sekoia Threat Detection and Research Team offer valuable guidance in mitigating the risks associated with Tycoon 2FA and related phishing attacks. By staying proactive and adopting a multi-layered approach to security, we can effectively combat this evolving menace and safeguard our digital assets. Together, we can create a safer online environment for all.

